Disclaimer: This is for use on a PC that you own. Breaking into someone else's PC is considered a serious crime in most places. If you make a mistake or change something else, your Windows may become a non-boot. If so, just undo whatever you changed outside of the hack shown here, and it will back to normal. Need I say this is for Educational Purposes! You are responsible for your own thoughts and actions.
Difficulty Level: 2/10
Prerequisites:
- Any Linux Live CD/DVD/USB with Live option (ex. Ubuntu Live, Linux Live, Kali, etc.).
- Ability to use said Linux CD/DVD/USB.
- Basic understanding of Windows file structure. i.e. can navigate.
- The desire to modify user account(s) on said Windows boxen.
- Physical access to said Windows box.
- Ability to use BIOS if needed.
- Ability to use command line and basic understanding of net user commands.
Things to Note:
- If you are trying to hack a coworker / boss / job / school / customer / friend / spouse's account, you are screwed because they won't be able to use the old password anymore—try explaining that.
- This hack works on Windows 7, 8, 10 and basically any that have "Ease of Access".
- Servers require "net user Administrator blabla /domain".
- This will destroy all data encrypted with EFS on the account if it's enabled (you have to enable it first).
- If you do not undo the hack after you change the password, you will get the magnifier every time you use cmd or nothing at all.
- If you modify or delete any other files in Sys32, your next boot up is doomed (maybe).
- Scared? You should be. Now let's get hacking.
Step 1Boot Some Flavor of Linux Live CD
Insert CD/DVD into drive and reboot the machine. Start your Live DVD. You may need to go into the BIOS screen and change the boot-up order to CD/DVD drive first, HDD second.
Step 2Navigate to Sys32
Use the file browser in your Linux environment, navigate to %windir%/system32/. You may have to right-click and mount the Windows partition/drive first or use the NTFS-3G command.
Step 3Rename Magnify.exe
Find and rename magnify.exe (Magnifier file) to magnify.old.
Step 4Rename cmd.exe
Find and rename cmd.exe to magnify.exe.
Step 5Shut Down Linux & Reboot Windows
Logout, remove DVD, and reboot into Windows.
Step 6Get CMD Prompt Modify Accounts
When Windows reboots, click on the ease of access button in the bottom left corner.
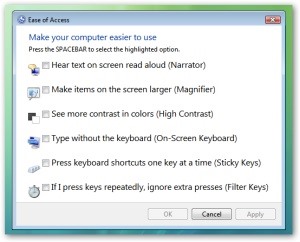
Click magnify and hit apply. Ta da. You have a system level command prompt. At this point is where we will only change the Admin password and not any of the 1000 other things that could be done at this point!
Tip: You can right-click on cmd.exe and click run as administrator inside of Windows for escalated privileges. To edit files, it would never be allowed at basic admin level (caution).
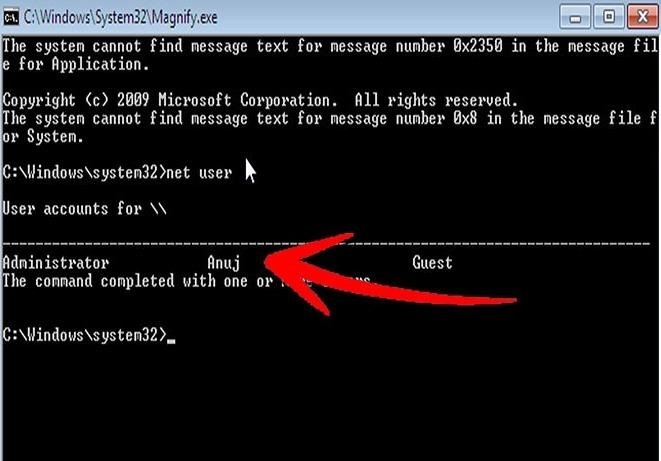
Image via whstatic.com
(Hacked system level command prompt. -Cx2H)
As the photo above shows, typenet user to get a list of accounts. To the point type: net user administrator *
Your Options (Choose One That Applies):
Change Password:
net user username new_password
When you do so, the password changes without prompting you again.
Add an account:
net user username password /add
Tip: If your username has a space, like John Doe, use quotes like "John Doe".
Admin that:
net localgroup administrators username /add
Delete that:
net user username /delete
Remote Desktop Users Group: (just in case)
net localgroup Remote Desktop Users UserLoginName /add
Net User Syntax Reference:
Domain i.e. Servers:
Step 7Reboot Linux & Fix magnfiy.exe
Now you should insert your Linux Live CD/DVD and rename the files back to original names or you will have issues later.
- Repeat Step 1
- Repeat Step 2
- Rename magnify.exe back to cmd.exe
- Rename magnify.old back to magnify.exe
- Log out, take out CD/DVD USB, reboot into Windows
Recommended Resources:
Conclusions:
Well, that was how you hack a Windows 7/8/10 etc. administrator account password with Windows Magnifier. This also demonstrates how you could Pwn a machine if you think about it some, have hands on and they have not disabled EoA. Hope it helps you in some way. Cx2H